刷题记录(4)
litctf
ezpy
这个文件一看是python打包的
然后本身解包很简单,但是找主函数调用的库找不到QAQ
但是exe可以执行,那么肯定库是在的
根据Pyinstaller打包的exe之一键反编译py脚本与防反编译_pyinstaller防止反编译-CSDN博客
查找资料,通过把PYZ-00.pyz打开查看内容找到最后的库
1 | pyi-archive_viewer ezpy.exe |
1 | x xxx.lib |
然后就和普通的操作一样了
CISCN
asm_re
这个是arm的汇编,看起来有点难QAQ
写脚本把代码跑出来又不是很现实
所以尝试丢给ai,写脚本解
1 | from prism import * |
androidso_re
感谢Z神的帮助,不然凭借我垃圾的安卓能力,一定会被吊死的QAQ
之后做安卓题的时候
先用die查看存档记录:
这个存档记录不知道什么意思,但是后面有写对应的安卓版本,如果使用dex编辑器可以看到mainactivity在classes3.dex中,
这个表明要用安卓7来打开它QAQ
之前试过用安卓10来调试,结果百分百寄,痛苦,用ida调so也断不了,QAQ
于是可以顺利用安卓7打开来调试
jadx:
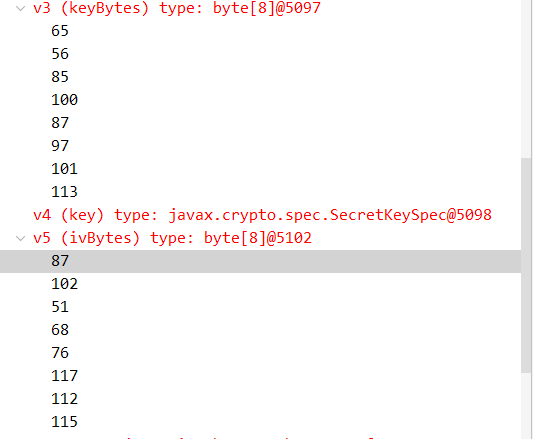
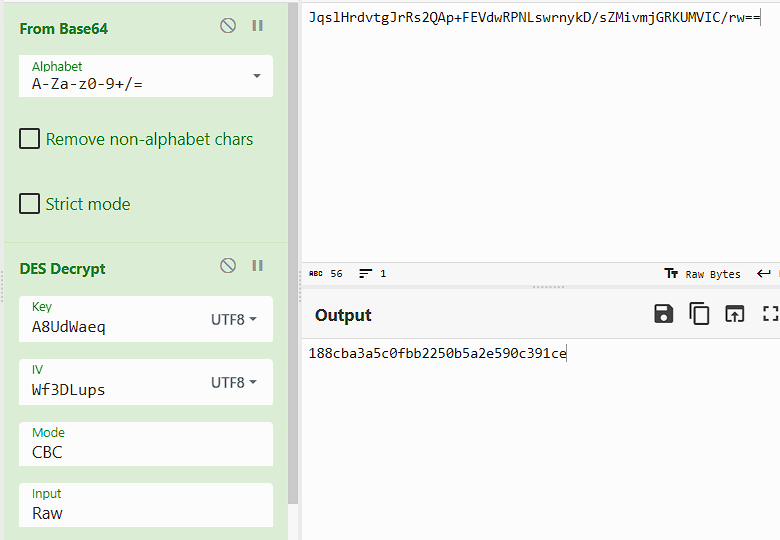
直接拿到密钥和iv
直接解
1 | flag{188cba3a5c0fbb2250b5a2e590c391ce} |
rust_baby
打开文件
随便调一下,看到一个一大串连续的指令,应该就是加密
看到有一堆base64,解一下
1 | { |
1 | { |
由于一开始看到了isdebugpresent,所以尝试了附加调试,但是调试的时候发现程序会直接退出
是因为这个程序有多个线程,这个时候不是main线程,这时要先切换到main线程再继续调试。
1 | 11111111111 |
不写了,shi
QAQ
go_reverse
go逆向
看到函数表
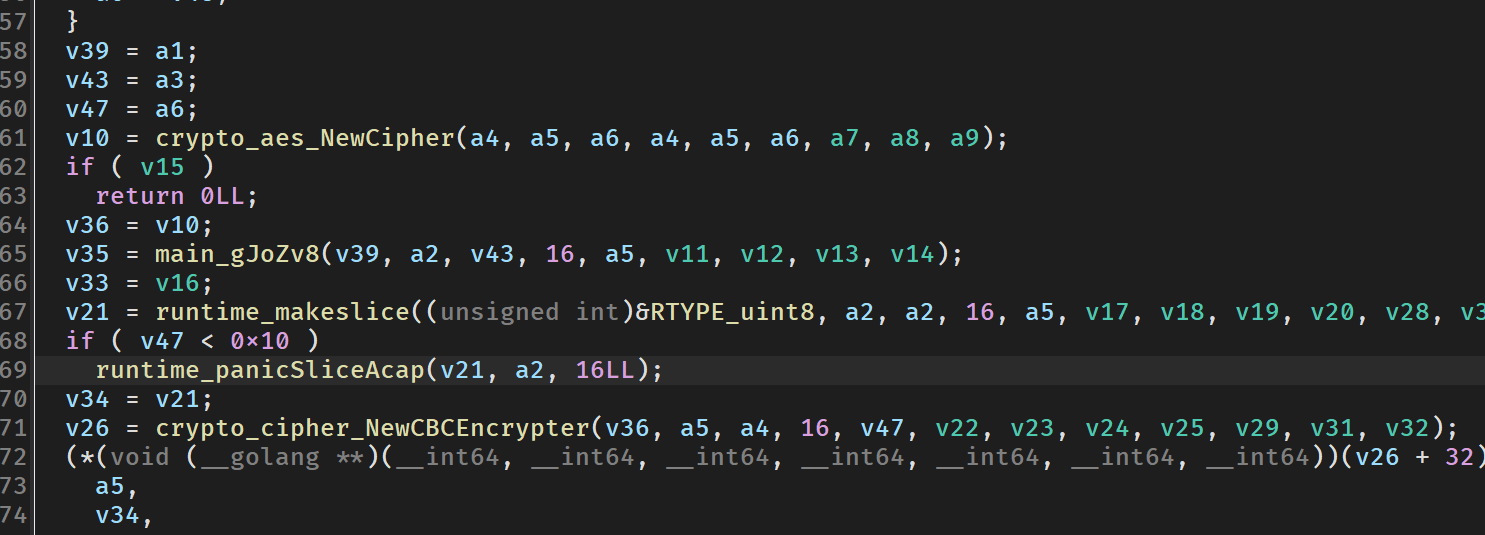
在main开头的函数里找到了这个
怀疑是aes cbc,经过分析,应该是
xor-tea-sm4-aes-base32
然后想了很久,硬是没发现flag是在哪里的,最后放弃,去找flag,发现那个题是环境题,题目只给了最后的secret
那么假定
1 | ZR23CZDIW3Q73KKTC3UJKENFAHFUFKOBNMM7FCHXGGY3BJY3B4FWQ4DCI5DQOEEMM5I6AZRABUNXA7CVWEDYKDOT4JLVSLE3WFGXI= |
这个是我的secret,QAQ
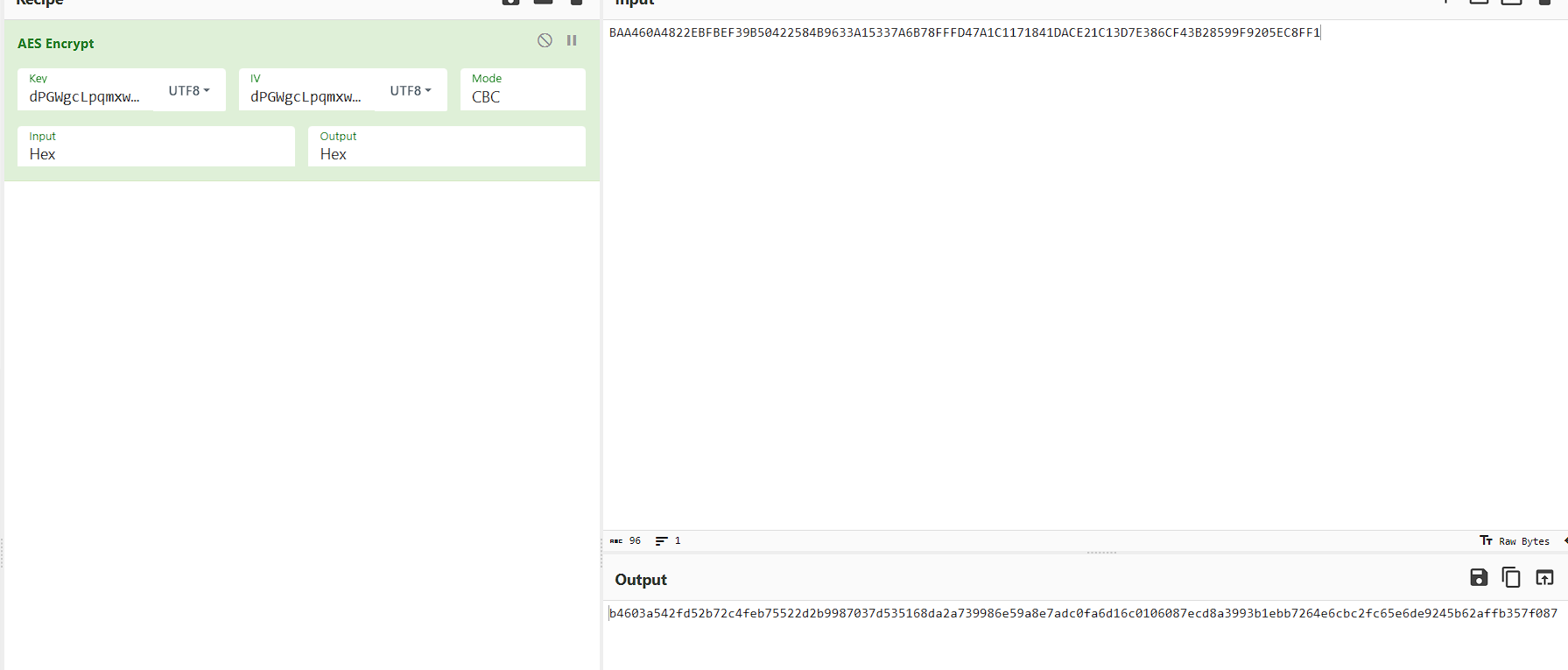
解完base32后解AES,这里看到了两个值
dPGWgcLpqmxw3uOXhKpKV009Cql和Bs^8*wZ4lu8oR&@k
第一个是密钥可以解密,第二个应该是iv
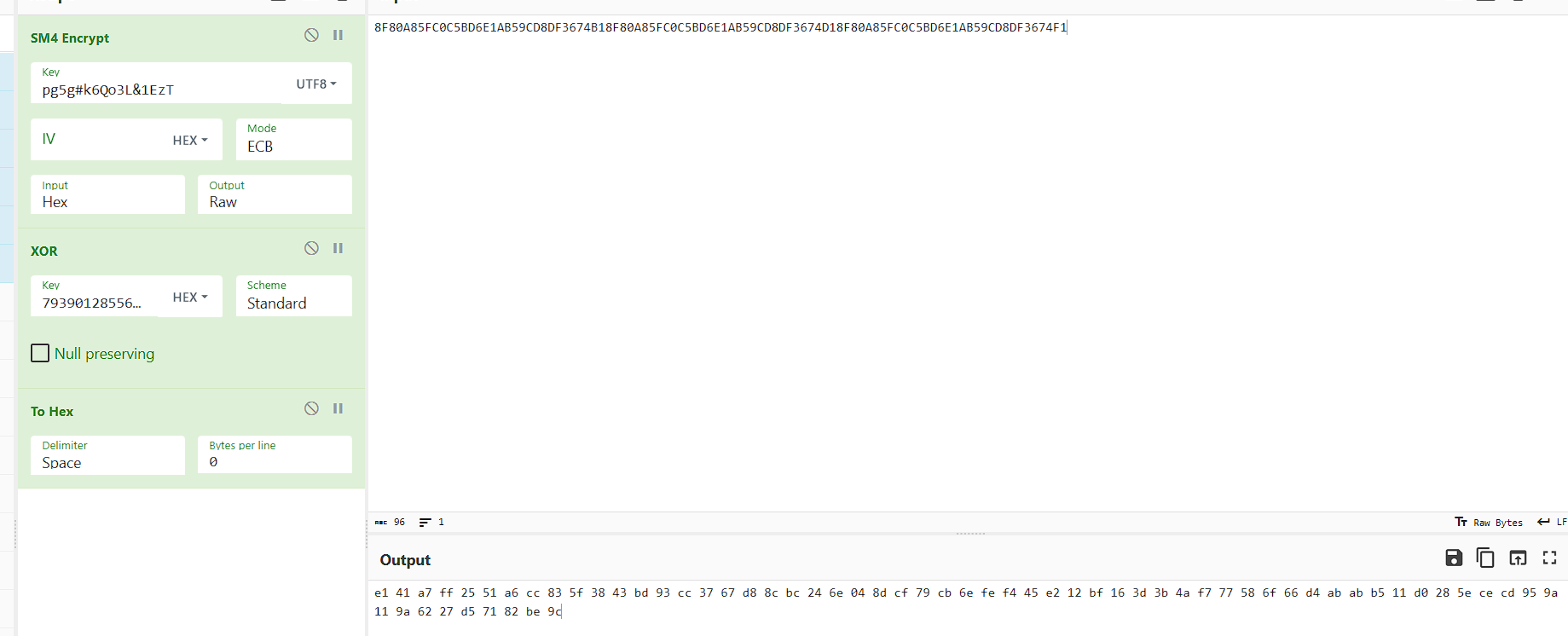
然后继续看sm4,传入了Bs^8*wZ4lu8oR&@kpg5g#k6Qo3L&1EzT
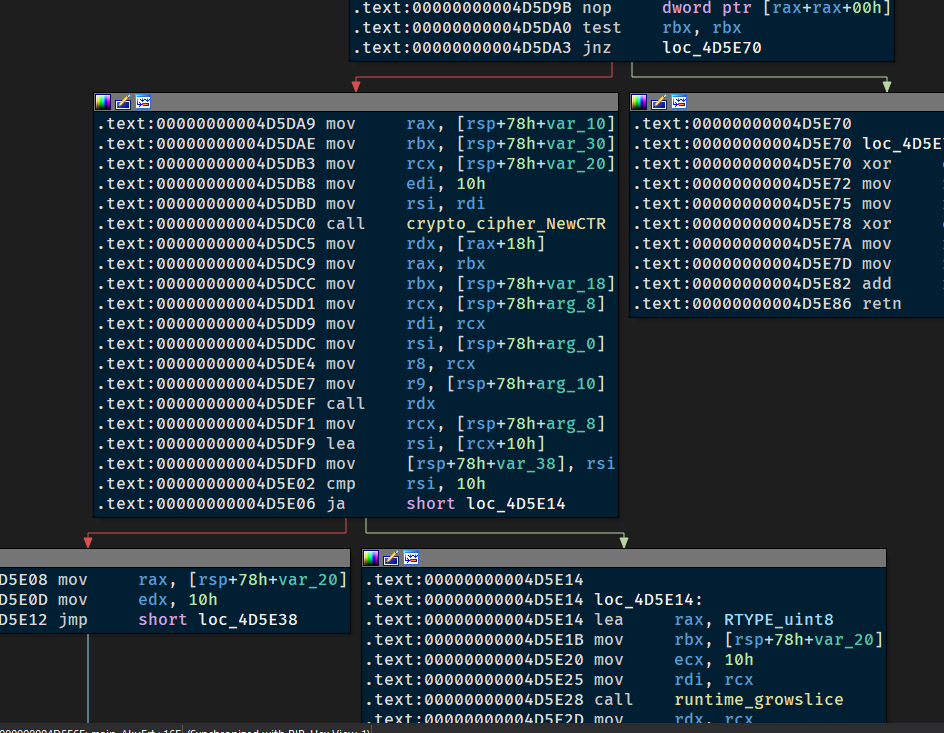
如果用流程图可以看到
这里说明了模式是CTR,逐步动调,分别可以看到一个128位值,一个16位值,和在自己写的flag下面两段相同的32位值,以及动调两步,在加密完后上面32位值下面添加了32位值
再动调,值没了
而下一步的输入
用这个可以猜aes的key和iv的值
发现key和iv是一样的,同理,后面也不知道SM4是怎么加密的
下面的调试步骤一共调了5次,可能数据对不上QAQ
观察输入和输出,已知key:pg5g#k6Qo3L&1EzT
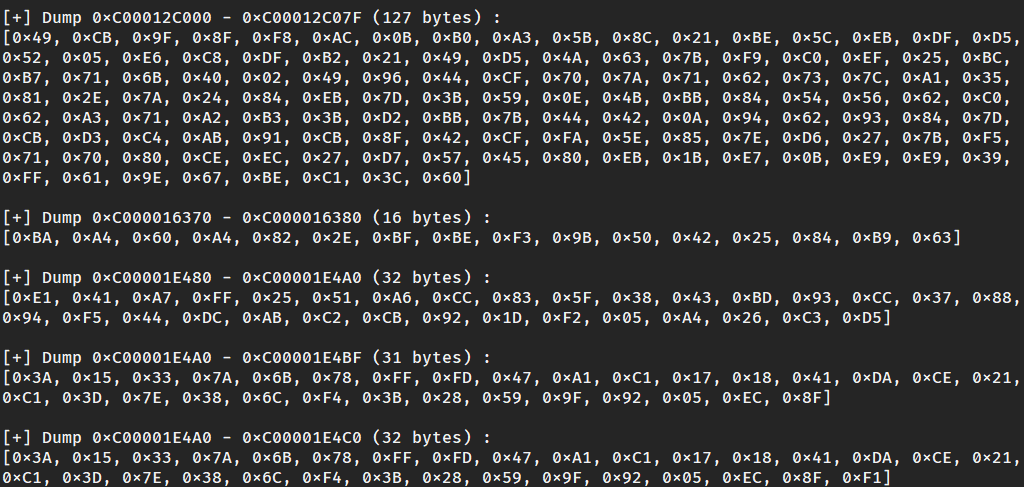
1 | [+] Dump 0xC00001E480 - 0xC00001E4A0 (32 bytes) : |
从32变成了48,sm4是块加密,一块为128位,16字节,输入正好是16的倍数,不应该增加位数,
再次调试,发现input是一样的,也就是说这里是先干了其它的然后才SM4
继续调试:可以推测128字节的值是s盒
在一个位置得到一个16长度的值s,值是
1 | [0xF5, 0xEE, 0x67, 0xFD, 0xD9, 0x8D, 0xD2, 0xA2, 0xCB, 0xAC, 0x8A, 0x44, 0x90, 0x17, 0xEB, 0xEC] |
下断点,发现它在加密中被读取了,并发现输入在后面被填充了
1 | [0x71, 0xBF, 0xC2, 0x5A, 0xAA, 0x6E, 0x9C, 0xA0, 0x45, 0x00, 0x68, 0xF3, 0x51, 0x07, 0x31, 0x3C] |
然后s被添加了值变成了
1 | [0x76, 0x6D, 0x54, 0x43, 0xEB, 0x59, 0x17, 0x36, 0xAE, 0xB1, 0xE0, 0x2C, 0xB3, 0x8C, 0x40, 0x44, 0x76, 0x6D, 0x54, 0x43, 0xEB, 0x59, 0x17, 0x36, 0xAE, 0xB1, 0xE0, 0x2C, 0xB3, 0x8C, 0x40, 0x64] |
有32个,后面添加的值只有最后一位从44变成了64
输入在后面添加了值
1 | [0x16, 0xCB, 0xBF, 0x5F, 0x3E, 0x55, 0x54, 0x17, 0x24, 0x77, 0x5C, 0xAB, 0x8F, 0xA1, 0x0D, 0x4E] |
rax保存了这个值,定位var28
重调:
在输入末尾
临近结束,这个状态还在,保存一下值
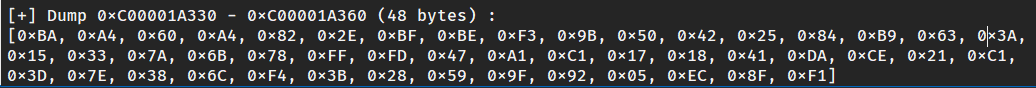
1 | input_ = [0xE1, 0x41, 0xA7, 0xFF, 0x25, 0x51, 0xA6, 0xCC, 0x83, 0x5F, 0x38, 0x43, 0xBD, 0x93, 0xCC, 0x37, 0x88, 0x94, 0xF5, 0x44, 0xDC, 0xAB, 0xC2, 0xCB, 0x92, 0x1D, 0xF2, 0x05, 0xA4, 0x26, 0xC3, 0xD5, 0x88, 0x8F, 0x9B, 0xCE, 0xD2, 0x3C, 0x34, 0x44, 0xE0, 0x4D, 0xC4, 0x45, 0x68, 0x56, 0x7A, 0x09, 0xC6, 0x70, 0x65, 0x34, 0x13, 0xF6, 0xC4, 0xF6, 0xFC, 0x15, 0x6E, 0x9C, 0xA5, 0x0F, 0x87, 0xCB] |
这里保存了p的前16个值,然后p变成了
1 | 0x88, 0x8F, 0x9B, 0xCE, 0xD2, 0x3C, 0x34, 0x44, 0xE0, 0x4D, 0xC4, 0x45, 0x68, 0x56, 0x7A, 0x09, 0xC6, 0x70, 0x65, 0x34, 0x13, 0xF6, 0xC4, 0xF6, 0xFC, 0x15, 0x6E, 0x9C, 0xA5, 0x0F, 0x87, 0xCB |
即input加长后的32位,有理由
1 | out = [0x6F, 0xA3, 0x58, 0x57, 0x08, 0x3C, 0x9F, 0x1F, 0x7A, 0x09, 0x4F, 0x56, 0xDD, 0x7D, 0x8D, 0xB9, 0x88, 0x8F, 0x9B, 0xCE, 0xD2, 0x3C, 0x34, 0x44, 0xE0, 0x4D, 0xC4, 0x45, 0x68, 0x56, 0x7A, 0x09, 0xC6, 0x70, 0x65, 0x34, 0x13, 0xF6, 0xC4, 0xF6, 0xFC, 0x15, 0x6E, 0x9C, 0xA5, 0x0F, 0x87, 0xCB] |
好好好,我理解了,看了一下CTR的定义,相当于其实是对计数器加密,然后和明文异或
然后还是没有发现第三个部分,看了网上的wp才知道有第三段QAQ
得到了明文
1 | 0xe1,0x41,0xa7,0xff,0x25,0x51,0xa6,0xcc,0x83,0x5f,0x38,0x43,0xbd,0x93,0xcc,0x37,0x67,0xd8,0x8c,0xbc,0x24,0x6e,0x04,0x8d,0xcf,0x79,0xcb,0x6e,0xfe,0xf4,0x45,0xe2,0x12,0xbf,0x16,0x3d,0x3b,0x4a,0xf7,0x77,0x58,0x6f,0x66,0xd4,0xab,0xab,0xb5,0x11,0xd0,0x28,0x5e,0xce,0xcd,0x95,0x9a,0x11,0x9a,0x62,0x27,0xd5,0x71,0x82,0xbe,0x9c |
然后解xxtea
1 |
啊啊啊啊啊啊啊啊啊啊啊啊啊啊,我谢谢你:)
解不出来放弃。QWQ
whereisThel1b
看佬的blog:
佬给了两个做法
硬分析:seed=0
秒
1 | import base64 |
愚者杯2023
ez_re
打开一看,是一个变体rc4,这算是我第一次遇见这种
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
这里的dword_DA3AA0是类似S盒的东西,但是有两个key,正常逆是逆不回去的,但是根据异或的性质,如果两个key一样,input和output正好可以相互解密,同时这是一个双射,一一对应,output就是v9的所有值,而key在循环中是加法,所以应当使用从最后到开始反着写,key组合一共只有90000种,而提示有base之后的flag值,由于最后的enc不能base回去,所以猜是先base后encode,flagbase之后是Zmxh,根据这个条件爆破
1 | for key1 in range(0,299): |
得到key:223和241和
1 | flag不在这里呦, |
然后看看加密矩阵,不理解,应该是说S盒,但是可以知道这个很长,并且是90000个数,不理解,看wp发现这是一个图片的单通道数据,作为红色
1 | from PIL import Image |
然后flag在图片中
1 | ctfshow{d244daeb-7182-4c98-bec6-0c99329ab71f} |
这真不是misc,不过下次应该就能想到了
CISCN好难啊啊啊啊
裂开
QAQ
不管了,还有好多东西没写