强网拟态2024复现
a_game
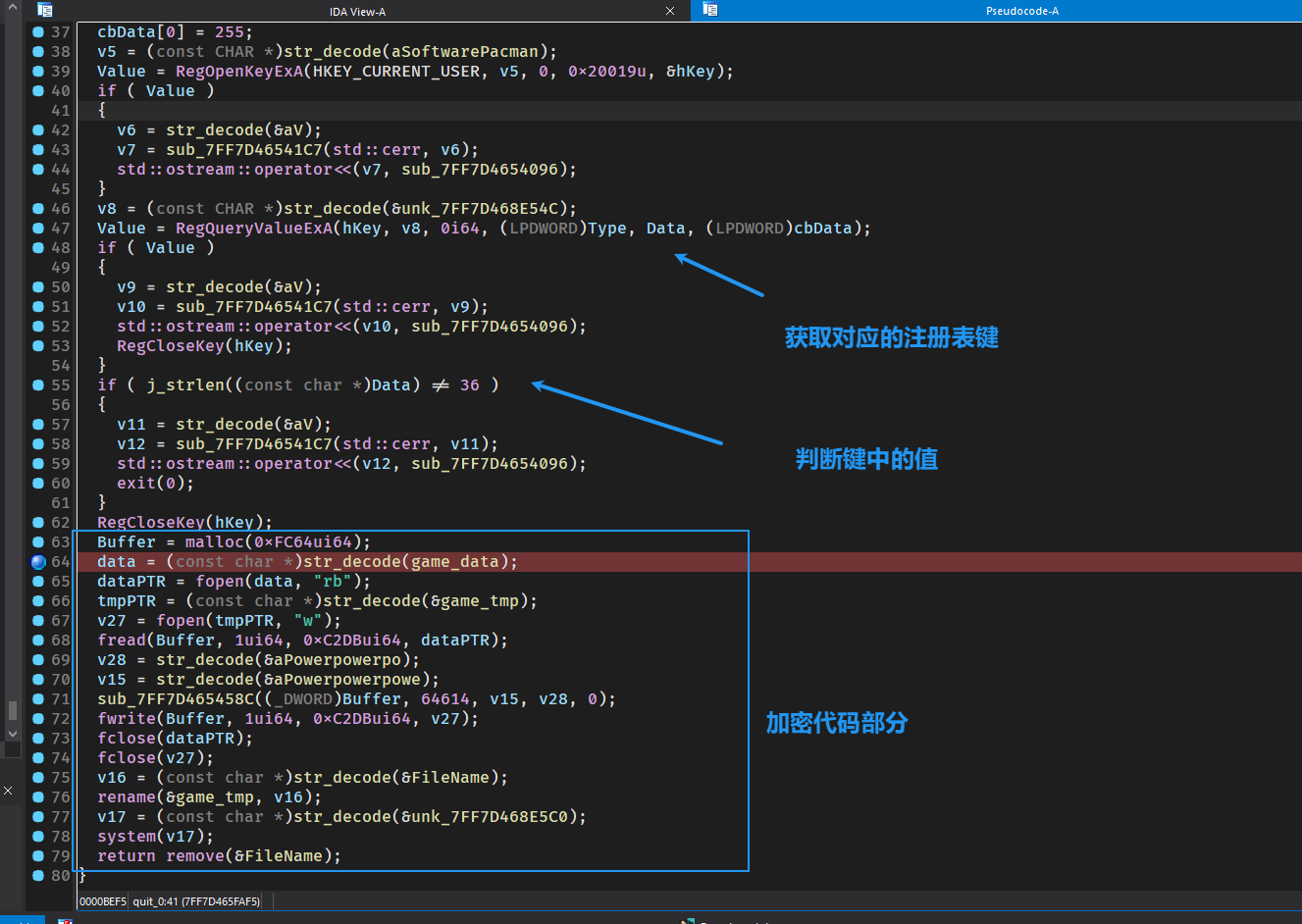
坑,我找了好久胜利的时候的条件,没想到是在退出的时候检查的QAQ,不过学到了注册表的相关函数,
把这里解密的脚本直接dump然后每次把最前面的函数名改成Write-Out输出没有混淆的版本,
比如:
1 | Write-Output( ( [RuntIme.INteroPsErviCEs.maRSHal]::PTrtostriNGAUTo( [rUNtIme.inteRopServIces.MarshAl]::seCuREsTrinGtobStr( $('76492d1116743f0423413b160省略base64内容' | conveRTTo-SECureSTrinG -K (94..117)) ) ))) |
这时可以直接在pwsh里执行,然后得到输出的代码,继续解密
然后继续直到解密出来代码
1 | function enenenenene { |
然后直接逆
1 | from prism import * |
servers
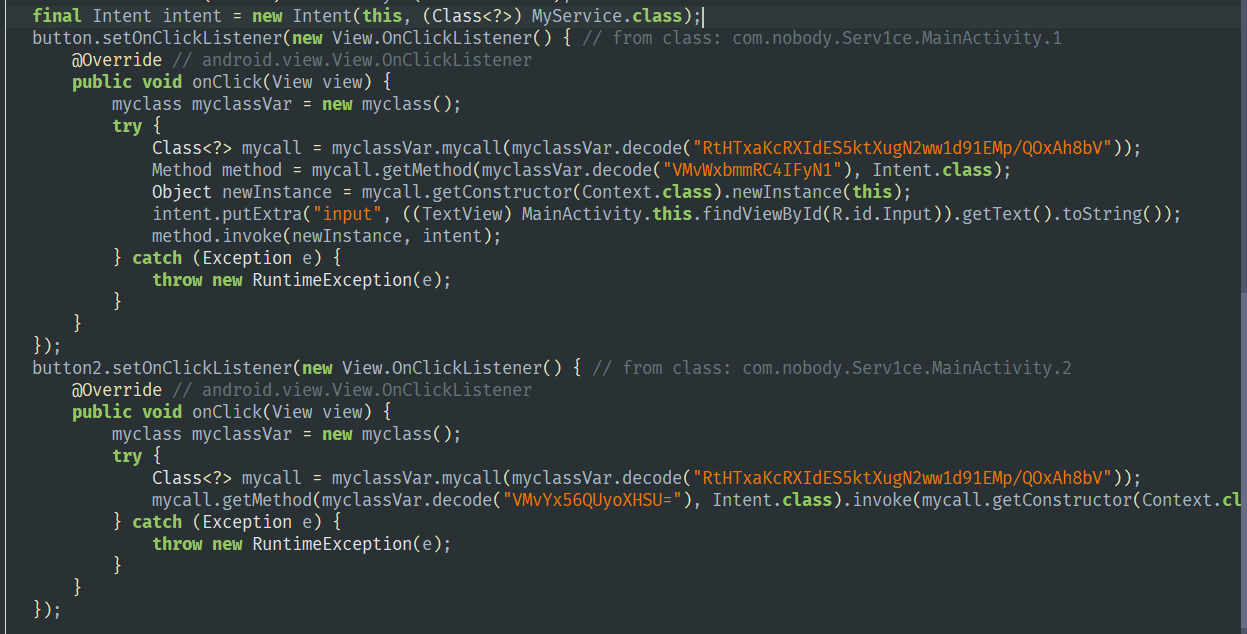
打开应用,发现有两个按钮input和check,对应了两个onClick函数
很明显用了动态加载类。尝试先对decode函数进行hook
得到
1 | myclass.decode is called: str=RtHTxaKcRXIdES5ktXugN2ww1d91EMp/QOxAh8bV |
1 | public void onCreate(Bundle bundle) { |
1 | final Intent intent = new Intent(this, (Class<?>) MyService.class); |
说明它用自己的service调用了startService
查看这个类
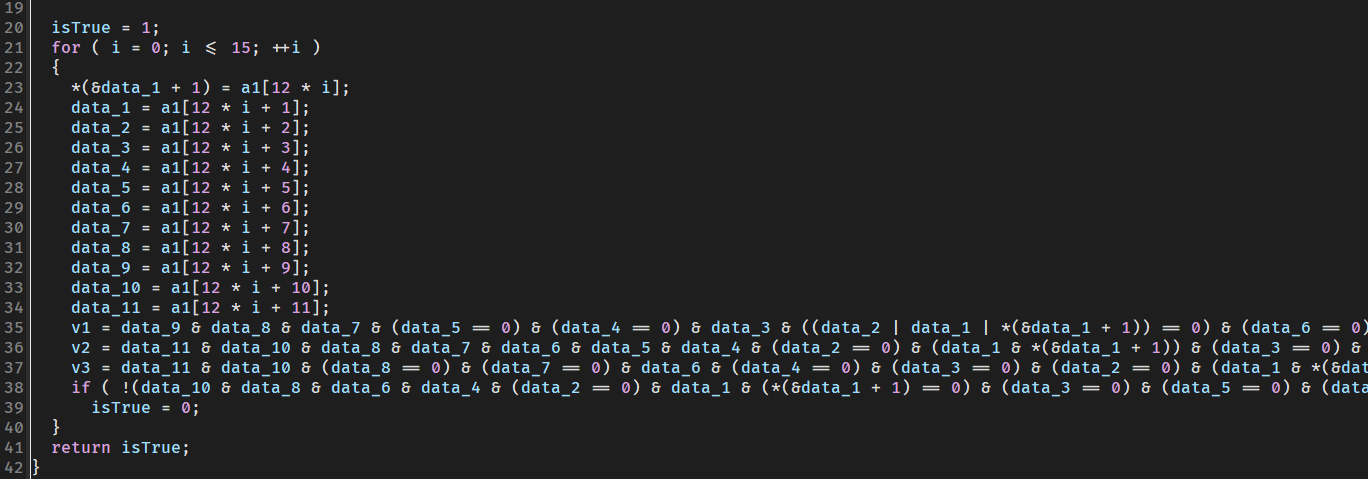
1 | private native boolean check(String str, byte[] bArr, int i); |
native函数
继续hook检查函数
得到
1 | bArr=-83,-30,-27,-59,-30,-83,-83,-30,-59,-30,-30,-59,-59,-30,-83,-83,-30,-30,-59,-59,-83,-30,-27,-59,-30,-83,-83,-30,-59,-30,-30,-59,-59,-30,-83,-83,-30,-30,-59,-59,-83,-30,-27,-59,-30,-83,-83,-30,-59,-30,-30,-59,-59,-30,-83,-83,-30,-30,-59,-59,-83,-30,-27,-59, i=11 |
得到最后检查值
然后看so文件,直接就有加密逻辑
1 | __int64 __fastcall Java_com_nobody_Serv1ce_MyService_check(JNIEnv *a1, jclass *a2, void *a3, void *a4, char a5) |
非常明显,直接爆破即可
1 | from prism import * |
baby_re
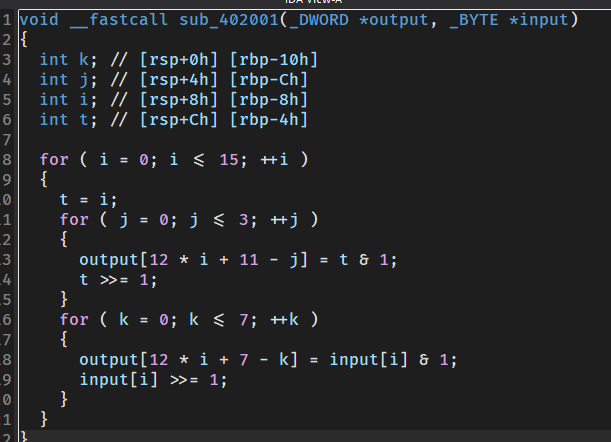
打开一看,第一个函数有很明显的AES特征,可以使用自己的值测试一下,发现确实是AES
第二段是一个将加密后每个输入切为bit,然后附上4位index值
最后一段的检查函数是bit的一堆运算,本来想用z3,但是z3类型一直报错,然后一想发现只有8+4位,直接开爆
1 | from prism import * |
最后有两个值,但是只有第一个是对的,不知道为什么。
ez_re
这个题一打开人就傻了,全是花,我该怎么分析流程呢
那就硬调吧QAQ
输入完之后步出,到这里,说明这之前在输入之前
然后转到data段开头,有一个56长度的数据,后面有一个0x12345678
猜测长度是56,对上面两个数据下断点,然后run
在某个地方断下来了(触发了0x12345678的断点),发现某个寄存器保存的输入被异或了
输入
1 | flag{11111111111111111111111111111111111111111111111111} |
输出
1 | 0x19, 0x13, 0x1E, 0x18, 0x04, 0x4E, 0x4E, 0x4E, 0x4E, 0x4E, 0x4E, 0x4E, 0x4E, 0x4E, 0x4E, 0x4E, |
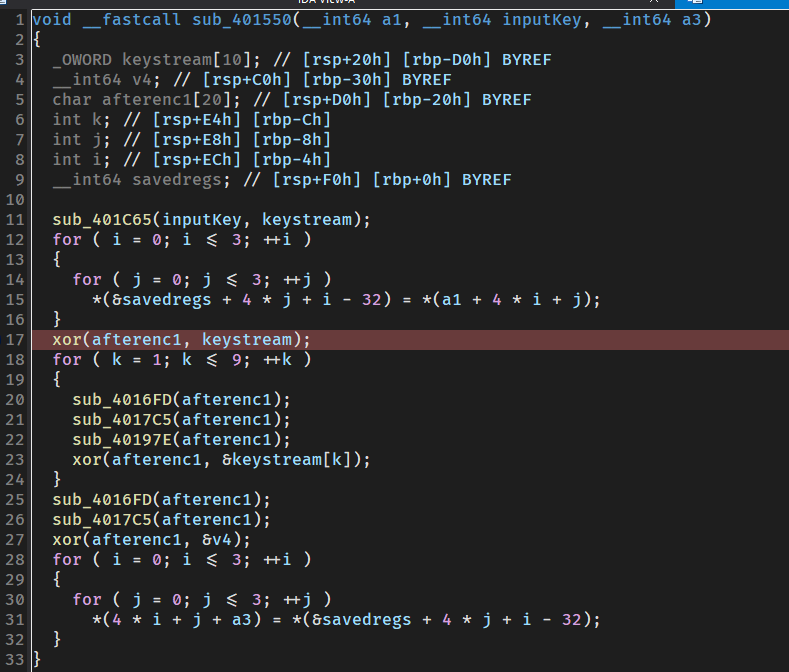
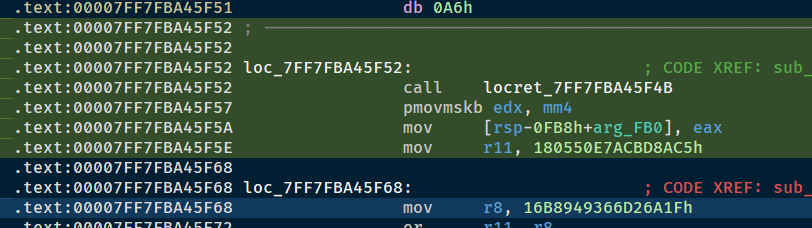
继续往后调,7FF7FBA45F18位置发现RAX变成了9E3779B9,有可能是Tea
后面会发现它把eax的值放到栈里面,接着就是这一次的加密数据
猜是个tea,然后不会了
评论